1Open the Connections page.
2Perform either of the following actions:
- - To create a connection, click New Connection and enter the connection details.
- - To edit a connection, click the connection name, and then click Edit.
3In the Connection Properties area, select Use Secret Vault.
4Enable the option next to each property that you store in the secrets manager, and then enter the path, including the secret name, in the corresponding field. If the secret is a JSON object, you'll also need to include the secret key.
The following table shows the value to enter based on the format of the secret:
Format of secret | Format of value to enter |
|---|---|
JSON object, for example: { "engine": "mysql", "username": "tsmith", "password": "Hello123", "host": "my-database-endpoint.us-west-2.rds.amazonaws.com", "dbname": "myDatabase", "port": "1234" } | <secret_path>:<key> Alternatively, if you use AWS Secrets Manager, you can enter the full ARN of the secret in the following format*: arn:aws:secretsmanager:<region>:<account_ID>:secret:<secret_name>-<6_random_characters>:<secret_path> |
Simple value, for example: --name "MyPassword" --value "Hello123" | <secret_path> Alternatively, if you use AWS Secrets Manager, you can enter the full ARN of the secret in the following format*: arn:aws:secretsmanager:<region>:<account_ID>:secret:<secret_name>-<6_random_characters> |
* If you use AWS Secrets Manager, and the account that hosts the Secure Agent differs from the account that hosts the secrets, you must enter the full ARN of the secret. | |
For example, you configure a relational connection and you store the database password in HashiCorp Vault. The path to the secret is secret/data/MyCredentials, and the secret key is MyPassword. To retrieve the password from HashiCorp Vault, select Use Secret Vault, enable the option next to the Password field, and enter secret/data/MyCredentials:MyPassword in the Password field.
The following image shows the connection details:
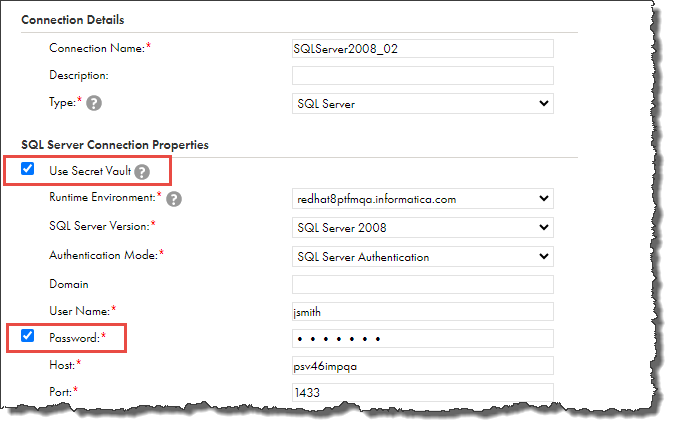
5Select the runtime environment to be used with the connection.
All Secure Agents within the runtime environment must be installed on a local machine or VM and must be able to access the secrets manager. Additionally, the SecretManagerApp service must be running on each agent.
6Configure the connection-specific properties.
7To test the connection, click Test Connection.
8Click Save.