Configuring Web Applications to Use Different Identity Providers
You can configure Informatica web applications that run in a domain to use different identity providers. For example, you might configure Informatica Administrator to use AD FS as the identity provider, and configure Informatica Analyst to use PingFederate as the identity provider.
When you enable a domain to use SAML authentication, all web applications that run in the domain use the default identity provider you specify when you enable SAML authentication in the domain. For example, if you configure AD FS as the identity provider, all web applications use AD FS as the identity provider, unless you configure a web application to use a different identity provider.
You specify the default identity provider when you use one of the following options to enable SAML authentication:
- •When you create the domain and install the Informatica services.
- •When you run the infasetup defineDomain command to create the domain.
- •When you run the infasetup updateDomainSamlConfig command to enable SAML authentication in an existing domain.
You use the Administrator tool to configure a web application to use a different identify provider. To configure the Administrator tool or the monitoring application to use a different identity provider, you modify the SAML configuration on the node where the application runs. To configure other web applications to use a different identity provider, you modify the SAML configuration within the application process.
Prepare to Use an Identity Provider
Complete the following tasks to prepare an Informatica web application to use an identity provider.
- 1. Create an LDAP configuration for the identity provider store that contains Informatica web application user accounts. You also create an LDAP security domain, and then import the user accounts into the security domain.
- 2. Export the identity provider assertion signing certificate from the identity provider.
- 3. Import the identity provider assertion signing certificate into a truststore file on each gateway node in the domain. You can import the certificate into the Informatica default truststore file, or into a custom truststore file.
If you change the alias name, import the corresponding certificate into the truststore file on each gateway node, and then restart the node.
- 4. Add one or more relying party trusts in the identity provider, and map LDAP attributes to the corresponding types used in security tokens issued by the identity provider.
- 5. Add the URL for the Informatica web application to the identity provider.
Configure Informatica Administrator to Use an Identity Provider
Use the Administrator tool to configure the Administrator tool or the monitoring application to use a SAML identity provider. You configure the Administrator tool or the monitoring application to use an identity provider on the node where the application runs.
1. In the Administrator tool, click the Services and Nodes tab.
2. Select the gateway node where the Administrator tool and the monitoring application run in the Domain Navigator.
3. Click the edit icon next to SAML Configuration.
4. Enter the properties required to enable the application to use an identity provider.
The following table describes the properties you enter:
Property | Description |
|---|
Identity Provider URL | Optional. The URL for the identity provider server. You must specify the complete URL string. |
Service Provider ID | Optional. The relying party trust name or the service provider identifier for the domain as defined in the identity provider. |
Assertion Signing Certificate Alias | Optional. The alias name specified when importing the identity provider assertion signing certificate into the truststore file used for SAML authentication. If you change the alias name, import the corresponding certificate into the truststore file on each gateway node, and then restart the node. |
Clock Skew Tolerance | Optional. The allowed time difference between the identity provider host system clock and the system clock on the master gateway node. Optional. The lifetime of SAML tokens issued by the identity provider by is set according to the identity provider host system clock. The lifetime of a SAML token issued by the identity provider is valid if the start time or end time set in the token is within the specified number seconds of the system clock on the master gateway node. Values must be from 0 to 600 seconds. Set to -1 to use the value configured for the domain. Default is 120 seconds. |
The following image shows the configuration to enable the Administrator tool to use AD FS as the identity provider. If you do not specify a value for a property, the domain uses the value set in the default SAML configuration.
5. Click OK.
6. Restart the application.
Configure an Informatica Web Application
Use the Administrator tool to configure an Informatica Web application to use a SAML identity provider.
1. In the Administrator tool, click the Services and Nodes tab.
2. Select the application or the application service in the Domain Navigator.
- - To configure the Analyst tool application to use an identity provider, select the Analyst Service, and then click the Processes tab.
- - To configure the Mass Ingestion tool application to use an identity provider, select the Mass Ingestion Service, and then click the Processes tab.
- - To configure the Metadata Manager application to use an identity provider, select the Metadata Manager Service, and then click the Properties tab.
- - To configure the Enterprise Data Catalog application or the Catalog Administrator application to use an identity provider, select the Catalog Service, and then click the Processes tab.
- - To configure the Enterprise Data Preparation application to use an identity provider, select the Enterprise Data Preparation Service, and then click the Processes tab.
- - To configure the Data Privacy Management application to use an identity provider, select the Data Privacy Management Service, and then click the Processes tab.
3. Click the edit icon next to SAML Configuration.
4. Enter the properties required to enable the web application to use an identity provider.
The following table describes the properties you enter:
Property | Description |
|---|
Identity Provider URL | Optional. The URL for the identity provider server. You must specify the complete URL string. |
Service Provider ID | Optional. The relying party trust name or the service provider identifier for the domain as defined in the identity provider. |
Assertion Signing Certificate Alias | Optional. The alias name specified when importing the identity provider assertion signing certificate into the truststore file used for SAML authentication. If you change the alias name, import the corresponding certificate into the truststore file on each gateway node, and then restart the node. |
Clock Skew Tolerance | Optional. The allowed time difference between the identity provider host system clock and the system clock on the master gateway node. Optional. The lifetime of SAML tokens issued by the identity provider by is set according to the identity provider host system clock. The lifetime of a SAML token issued by the identity provider is valid if the start time or end time set in the token is within the specified number seconds of the system clock on the master gateway node. Values must be from 0 to 600 seconds. Default is 120 seconds. |
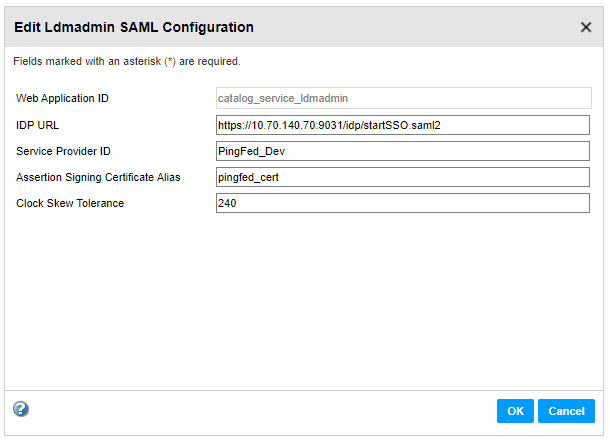
The following image shows the configuration to enable Enterprise Data Catalog to use PingFederate as the identity provider:
5. Click OK.
6. Restart the application or application service after you configure an application to use a SAML identity provider.