Preparing to Enable Kerberos Authentication
You must complete multiple tasks to prepare to enable Kerberos authentication in an Informatica domain. The procedures you follow for each task depend on the service principal level at which you enable Kerberos.
Note: You cannot disable Kerberos authentication in a domain after you enable it. You also cannot switch the service principal level between the node level and the process level.
Determine the Kerberos Service Principal Level
When you prepare to enable Kerberos authentication, you must determine the required service principal level. The required service principal level determines the procedures you must follow to prepare to enable Kerberos authentication in the domain.
You can enable Kerberos authentication at one of the following levels:
- Node Level
If you use the domain for testing or development, and the domain does not require a high level of security, you can enable Kerberos at the node level. You can use a single service principal name and a single keytab file for the node and for all of the processes and services that run on the node. You must also create a an SPN and a keytab file for the HTTP processes that run on the node.
- Process Level
If you use the domain for production, and the domain requires a high level of security, you can set the service principal at the process level. You create a unique SPN and keytab file for each node and each process on the node. You must also create a an SPN and a keytab file for the HTTP processes that run on the node.
Kerberos enabled at the process level provides the highest level of security, but might be difficult to manage in an Informatica domain that contains many nodes or has many services. In this scenario, you might want to enable Kerberos at the node level.
Configure the Kerberos Configuration File
Set the properties required by Informatica in the Kerberos configuration file, and then copy the file to each node in the Informatica domain.
Kerberos stores configuration information in a file named krb5.conf. You must set the properties in the krb5.conf configuration file and then copy the file to every node in the Informatica domain.
If the domain uses Kerberos cross realm authentication, enter the required properties for each Kerberos realm.
1. Configure the following Kerberos library properties in the libdefaults section of the file.
The following table describes the properties to enter:
Property | Description |
|---|
default_realm | Name of the Kerberos realm to which the Informatica domain services belong. The realm name must be in uppercase. If the domain uses a single Kerberos realm for authentication, the service realm name and the user realm name must be the same. |
forwardable | Allows a service to delegate client user credentials to another service. The Informatica domain requires application services to authenticate the client user credentials with other services. Set to true. |
default_tkt_enctypes | Encryption types for the session key included in ticket-granting tickets (TGT). Set this property only if session keys must use specific encryption types. Ensure that the Kerberos Key Distribution Center (KDC) supports the encryption type that you specify. Do not set this property to allow the Kerberos protocol to select the encryption type to use. If the node hosts or Informatica client hosts use 256-bit encryption, install the Java Cryptography Extension (JCE) unlimited strength policy files on all node hosts and Informatica client hosts to avoid authentication issues. |
rdns | Determines whether reverse name lookup is used in addition to forward name lookup to canonicalize host names for use in service principal names. Set to false. |
renew_lifetime | The default renewable lifetime for initial ticket requests. |
ticket_lifetime | The default lifetime for initial ticket requests. |
udp_preference_limit | Determines the protocol that Kerberos uses when it sends a message to the KDC. Set to 1 to use the TCP protocol if the domain experiences intermittent Kerberos authentication failures. |
dns_lookup_kdc | Indicates whether the Kerberos client uses DNS SRV records to locate the KDCs and other servers for a realm, if they are not listed in the information for the realm. DNS uses SRV records to identify computers that host specific services. Required when the domain is Kerberos-enabled. Requires you to set the admin_server realm property. Set to true. |
dns_lookup_realm | Indicates whether the Kerberos client uses DNS TXT records to determine the Kerberos realm of a host. DNS uses text or TXT records to associate arbitrary text with a host or other name, such as human readable information about a server, network, data center, or other accounting information. Required when the domain is Kerberos-enabled. Set to true. |
2. Define each Kerberos realm in the realms section of the file.
The following example shows the entry for a Kerberos realm named COMPANY.COM:
[realms]
COMPANY.COM = {...}
3. Enter the following realm properties inside the brackets for each Kerberos realm in the realms section of the file.
The following table describes the properties to enter:
Property | Description |
|---|
admin_server | The name or IP address of the Kerberos administration server host. You can include an optional port number, separated from the host name by a colon. Default is 749. Required if you configure dns_lookup_kdc in the libdefaults section. |
kdc | The name or IP address of a host running the Key Distribution Center (KDC) for the realm. You can include an optional port number, separated from the host name by a colon. Default is 88. |
The following example shows the entries for each Kerberos realm in a Kerberos cross realm configuration:
[realms]
COMPANY.COM = {
admin_server = KDC01.COMPANY.COM:749
kdc = KDC01.COMPANY.COM:88
}
EAST.COMPANY.COM = {
kdc = 10.75.141.193
admin_server = 10.75.141.193
}
WEST.COMPANY.COM = {
kdc = 10.78.140.111
admin_server = 10.78.140.111
}
4. In the domain_realms section, map the domain name or host name to a Kerberos realm name. The domain name is prefixed by a period (.).
The following example shows the parameters for the Hadoop domain_realm if the Informatica domain does not use Kerberos authentication:
[domain_realm]
.hadoop_realm.com = HADOOP-REALM
hadoop_realm.com = HADOOP-REALM
The following example shows the parameters for the Hadoop domain_realm if the Informatica domain uses Kerberos authentication:
[domain_realm]
.infa_ad_realm.com = INFA-AD-REALM
infa_ad_realm.com = INFA-AD-REALM
.hadoop_realm.com = HADOOP-REALM
hadoop_realm.com = HADOOP-REALM
5. Copy the krb5.conf file to the following locations on the machine that hosts the Data Integration Service:
- - <Informatica installation directory>/services/shared/security/
- - <Informatica installation directory>/java/jre/lib/security
The following example shows the content of a Kerberos configuration file with the required properties for a single Kerberos realm configuration:
[libdefaults]
default_realm = COMPANY.COM
forwardable = true
rdns = false
renew_lifetime = 7d
ticket_lifetime = 24h
udp_preference_limit = 1
dns_lookup_kdc = true
dns_lookup_realm = true
[realms]
COMPANY.COM = {
admin_server = KDC01.COMPANY.COM:749
kdc = KDC01.COMPANY.COM:88
}
[domain_realm]
.company.com = COMPANY.COM
company.com = COMPANY.COM
The following example shows the content of a Kerberos configuration file with the required properties for a Kerberos cross realm configuration:
[libdefaults]
default_realm = COMPANY.COM
forwardable = true
rdns = false
renew_lifetime = 7d
ticket_lifetime = 24h
udp_preference_limit = 1
dns_lookup_kdc = true
dns_lookup_realm = true
[realms]
COMPANY.COM = {
admin_server = KDC01.COMPANY.COM:749
kdc = KDC01.COMPANY.COM:88
}
EAST.COMPANY.COM = {
kdc = 10.75.141.193
admin_server = 10.75.141.193
}
WEST.COMPANY.COM = {
kdc = 10.78.140.111
admin_server = 10.78.140.111
[domain_realm]
.company.com = COMPANY.COM
company.com = COMPANY.COM
.east.company.com = EAST.COMPANY.COM
east.company.com = EAST.COMPANY.COM
.west.company.com = WEST.COMPANY.COM
west.company.com = WEST.COMPANY.COM
For more information about the Kerberos configuration file, see the Kerberos network authentication documentation.
Create Kerberos Principal Accounts in Active Directory
Create LDAP user accounts for the Kerberos principals in Active Directory. A Kerberos principal is a process, service, or user within the Kerberos realm.
If you set the default_tkt_enctypes property in the krb5.conf configuration file to the 128-bit or 256-bit AES encryption types, configure each account to use the corresponding encryption type in Active Directory.
The accounts that you create depend on whether you enable Kerberos at the node level or at the process level.
Note: Account names can be a maximum of 20 characters in length.
Accounts Required at Node Level
Create the LDAP user accounts required to enable Kerberos authentication at the node level in Active Directory.
Create the following Kerberos principal accounts in Active Directory if you enable Kerberos at the node level:
- Node processes
- Create an account for each node that runs in the domain.
- HTTP process
- Create an account for the Informatica web applications that run on a node in the domain. Web applications that run on a node might include the Administrator tool, Informatica Analyst, and Catalog Administrator. Create a single account that is shared by all of the web applications that run on the node.
- Bind User Distinguished Name (DN)
- Create an LDAP bind user account that you use to synchronize the LDAP security domain that contains Kerberos user accounts with Active Directory.
Accounts Required at Process Level
Create the LDAP user accounts required to enable Kerberos authentication at the process level in Active Directory.
Create the following Kerberos principal accounts in Active Directory if you enable Kerberos at the process level:
- Node processes
- Create an account for each node that runs in the domain.
- HTTP processes
- Create an account for the Informatica web applications that run on a node in the domain. Web applications that run on a node might include Informatica Analyst and Catalog Administrator. Create a single account that is shared by all of the web applications that run on the node.
- Informatica Administrator service
- Create an account for the Administrator tool on each gateway node in the domain.
- Informatica application services
- Create an account for every Informatica application service that runs on each node in the domain.
- Bind User Distinguished Name (DN)
- Create an LDAP user account that you use to synchronize the LDAP security domain that contains Kerberos user accounts with Active Directory.
Generate the Service Principal Name and Keytab File Name Formats
Use the Informatica Kerberos SPN Format Generator utility to generate the service principal name (SPN) and keytab file name formats required to use Kerberos authentication. The Kerberos SPN Format Generator utility generates a text file named SPNKeytabFormat.txt that contains the correct format for the SPNs and keytab file names.
The SPN and keytab file name formats you generate depend on whether you enable Kerberos at the node level or at the process level.
Generate the Service Principal Name and Keytab File Name Formats at Node Level
Generate the formats for the SPNs and keytab file names required to enable Kerberos authentication at the node level.
The Informatica domain requires SPNs and keytab files for the following processes when you enable Kerberos authentication at the node level:
- Node processes
- Informatica requires an SPN and keytab file for every node in the domain. Kerberos uses the same service principal name and keytab to authenticate the Informatica application services that run on the node.
- HTTP processes
- Informatica requires an SPN and keytab file for the web applications that run on each node in the domain. Web applications that run on a node might include the Administrator tool, Informatica Analyst and Catalog Administrator. Kerberos uses the same service principal name to authenticate all of the web applications that run on the node.
1. On a Windows Informatica node host, go to the directory that contains the SPNFormatGenerator.bat batch file:
<Informatica installation directory>\tools\Kerberos
On a UNIX Informatica node host, go to the directory that contains the SPNFormatGenerator.sh shell file:
<Informatica installation directory>/tools/Kerberos
2. Run SPNFormatGenerator.bat or SPNFormatGenerator.sh.
3. Click Next.
4. Select Node Level.
5. Click Next.
6. Enter the properties required to generate the SPN and keytab file formats.
The following table describes the properties:
Prompt | Description |
|---|
Domain Name | Name of the Informatica domain. The name must not exceed 128 characters and must be 7-bit ASCII. It cannot contain a space or any of the following characters: ` % * + ; " ? , < > \ / |
Service Realm Name | Name of the Kerberos realm. The realm name must be in uppercase. |
Node Name | Name of the Informatica node. |
Node Host Name | Fully qualified name of the node host. The node host name cannot contain the underscore (_) character. Note: Do not use localhost. The host name must explicitly identify the host. |
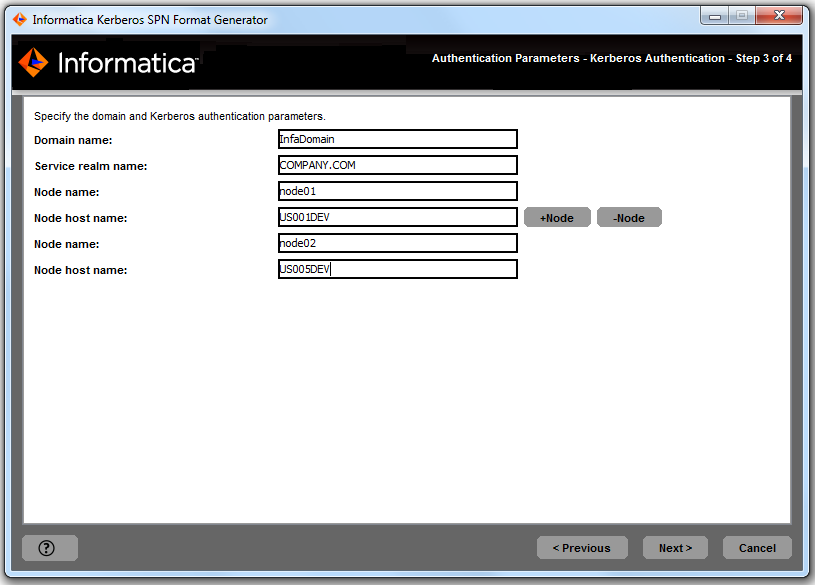
7. To generate the SPN format for an additional node, click +Node and specify the node name and host name.
The following image shows the entries for multiple nodes in the InfaDomain domain in the SPN Format Generator utility:
8. Click Next.
The SPN Format Generator utility displays the path and file name of the file that contains the list of service principal names and keytab file names.
9. Click Done to exit the SPN Format Generator utility.
Generate the Service Principal Name and Keytab File Name Formats at Process Level
Generate the formats for the SPNs and keytab file names required to enable Kerberos authentication at the process level.
The Informatica domain requires SPNs and keytab files for the following processes and services when you enable Kerberos authentication at the process level:
- Node processes
- Informatica requires an SPN and keytab file for every node in the domain.
- Informatica Administrator
- Informatica requires an SPN and keytab file for the Administrator tool for every gateway node in the domain.
- HTTP processes
- Informatica requires an SPN and keytab file for the web applications that run on a node in the domain. Web applications that run on a node might include Informatica Analyst and Catalog Administrator.
- Informatica application service processes
- Informatica requires an SPN and keytab file for each Informatica application service that runs on every node in the domain.
1. On a Windows Informatica node host, go to the directory that contains the SPNFormatGenerator.bat batch file:
<Informatica installation directory>\tools\Kerberos
On a UNIX Informatica node host, go to the directory that contains the SPNFormatGenerator.sh shell file:
<Informatica installation directory>/tools/Kerberos
2. Run SPNFormatGenerator.bat or SPNFormatGenerator.sh.
3. Click Next.
4. Select Process Level.
5. Click Next.
6. Enter the properties required to generate the SPN and keytab file formats.
The following table describes the properties:
Prompt | Description |
|---|
Domain Name | Name of the Informatica domain. The name must not exceed 128 characters and must be 7-bit ASCII. It cannot contain a space or any of the following characters: ` % * + ; " ? , < > \ / |
Service Realm Name | Name of the Kerberos realm. The realm name must be in uppercase. |
Node Name | Name of the Informatica node. |
Node Host Name | Fully qualified name or the IP address of the node host. The node host name cannot contain the underscore (_) character. Note: Do not use localhost. The host name must explicitly identify the host. |
7. To generate the SPN format for an Informatica application service that runs on a node, click Service after entering the node details.
Enter the name of the Informatica application service as shown in the Administrator tool. Complete this step for each Informatica application service that runs on each node in the domain.
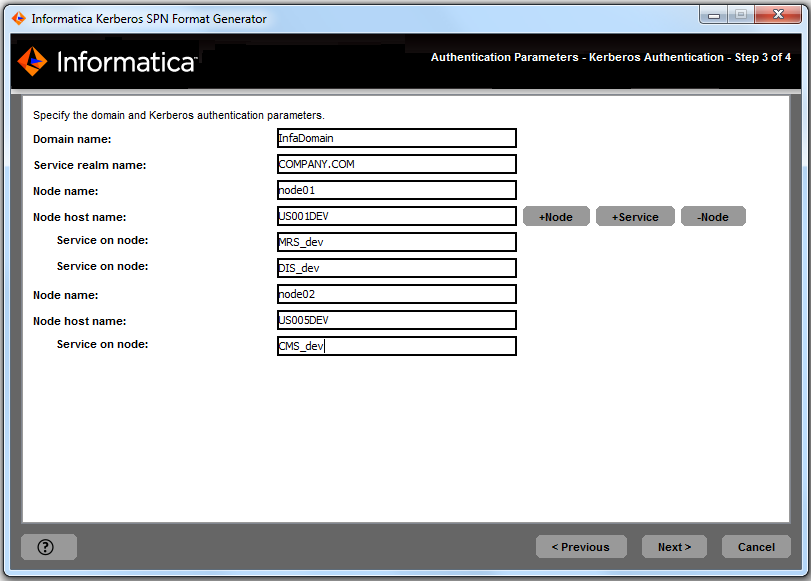
8. To generate the SPN format for an additional node, click +Node and specify the node name and host name.
The following image shows the entries for multiple nodes and application services that run in the InfaDomain domain in the SPN Format Generator utility:
9. Click Next.
The SPN Format Generator utility displays the path and file name of the file that contains the list of service principal names and keytab file names.
10. Click Done to exit the SPN Format Generator utility.
Review the Service Principal Name and Keytab File Name Format Text File
After you generate the SPNKeytabFormat.txt file, you can review the file.
You use the information in the file to generate the keytab files, and to associate each SPN with the corresponding principal user account in Active Directory.
The SPNKeytabFormat.txt file contains the following information:
- Entity Name
- Identifies the node or service associated with the process.
- Service Principal Name
- Format for the SPN. The SPN is case sensitive.
Note: If you enter a string containing multiple Kerberos domain names, or add an asterisk before a realm suffix to include all realms that include the suffix, the SPN format does not include the realm name.
- The following table describes the SPN formats:
Keytab type | SPN Format |
|---|
NODE_SPN | isp/<node name>/<domain name>@<REALM NAME> |
NODE_AC_SPN | _AdminConsole/<node name>/<domain name>@<REALM NAME> |
NODE_HTTP_SPN | HTTP/<node host name>@<REALM NAME> Note: The Kerberos SPN Format Generator validates the node host name. If the node host name is not valid, the utility does not generate an SPN. Instead, it displays the following message: Unable to resolve host name. |
SERVICE_PROCESS_SPN | <application service name>/<node name>/<domain name>@<REALM NAME> |
- Keytab File Name
- Format for the name of the keytab file to be created for the associated SPN. The keytab file name is case sensitive.
- The following table describes the keytab file name formats:
Keytab Type | Keytab File Name |
|---|
NODE_SPN | <node name>.keytab |
NODE_AC_SPN | _AdminConsole.keytab |
NODE_HTTP_SPN | webapp_http.keytab |
SERVICE_PROCESS_SPN | <application service name>.keytab |
Service Principals at Node Level
The following image shows the contents of the SPNKeytabFormat.txt file generated for service principals at the node level:
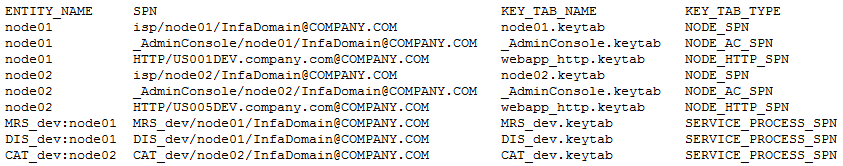
Service Principals at Process Level
The following image shows the contents of the SPNKeytabFormat.txt file generated for service principals at the process level:
Generate the Keytab Files
Generate the keytab files used to authenticate Informatica users and services.
You use the Microsoft Windows Server ktpass utility to generate a keytab file for each user account you created in Active Directory. You must generate the keytab files on a member server or on a domain controller within the Active Directory domain. You cannot generate keytab files on a workstation operating system such as Microsoft Windows 7.
To use ktpass to generate a keytab file, run the following command:
ktpass.exe -out <keytab filename> -princ <service principal name> -mapuser <user account> [-pass <user account password>] -crypto <key types> -ptype <principal type> [-target <realm name>]
The following table describes the command options:
Option | Description |
|---|
-out | The file name of the Kerberos keytab file to generate as shown under the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. |
-princ | The service principal name displayed under the SPN column in the SPNKeytabFormat.txt file. If the domain uses Kerberos cross realm authentication, the service principal name must be unique across all Kerberos realms. |
-mapuser | The Active Directory user account to associate with the SPN. The account name can be a maximum of 20 characters. |
-pass | The password set in Active Directory for the Active Directory user account, if applicable. |
-crypto | Specifies the key types generated in the keytab file. Set to all to use all supported cryptographic types. |
-ptype | The principal type. Set to KRB5_NT_PRINCIPAL. |
-target | The name of the realm to which the Active Directory server belongs. Include this option if the following error occurs when you run the utility: DsCrackNames returned 0x2 in the name |
The keytab files you generate depends on whether you enable Kerberos at the node level or at the process level.
Generate the Keytab Files at Node Level
When you run ktpass to generate the keytab files at the node level, you associate each Kerberos principal user account with the corresponding SPN in Active Directory.
The following table shows the association between the Kerberos principal user accounts and the SPNs shown in the example SPNKeytabFormat.txt file:
User Account | Keytab Type | Service Principal Name |
|---|
nodeuser01 | NODE_SPN | isp/node01/InfaDomain/COMPANY.COM |
httpuser01 | NODE_HTTP_SPN | HTTP/US001DEV.company.com@COMPANY.COM |
nodeuser02 | NODE_SPN | isp/node02/InfaDomain/COMPANY.COM |
httpuser02 | NODE_HTTP_SPN | HTTP/US005DEV.company.com@COMPANY.COM |
You also create a keytab for the LDAP bind user account that is used to access and search Active Directory during LDAP synchronization.
1. Create a keytab file for the Kerberos principal user account that you created for each node in Active Directory.
Copy the keytab file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a Kerberos principal user account named nodeuser0:
ktpass.exe -out node01.keytab -princ isp/node01/InfaDomain/COMPANY.COM -mapuser nodeuser01 -crypto all -ptype KRB5_NT_PRINCIPAL
2. Create a keytab file for each HTTP process Kerberos principal user account that you created in Active Directory.
If the domain uses Kerberos cross realm authentication, the principal user account can exist in any Kerberos realm the domain uses.
Copy the keytab file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a Kerberos principal user account named httpuser01:
ktpass.exe -out webapp_http.keytab -princ HTTP/US001DEV.company.com@COMPANY.COM -mapuser httpuser01 -crypto all -ptype KRB5_NT_PRINCIPAL
3. Create a keytab for the LDAP bind user account that is used to access and search Active Directory during LDAP synchronization.
Structure the value for the -princ option as <principal name>@<KERBEROS REALM>. Include the name of the LDAP configuration for the Active Directory server in the keytab file name. Structure the keytab file name as follows: <Active Directory LDAP configuration_name>.keytab.
The following example creates a keytab file for a service principal user account named ldapuser:
ktpass.exe -out ActiveDirectoryServer1.keytab -princ ldapuser@COMPANY.COM -mapuser ldapuser -crypto all -ptype KRB5_NT_PRINCIPAL
Generate the Keytab Files at Process Level
When you run ktpass to generate the keytab files at the process level, you associate each Kerberos principal user account with the corresponding SPN in Active Directory.
The following table shows the association between the Kerberos principal user accounts and the SPNs shown in the example SPNKeytabFormat.txt file:
User Account | Keytab Type | Service Principal Name |
|---|
nodeuser01 | NODE_SPN | isp/node01/InfaDomain/COMPANY.COM |
admintooluser01 | NODE_AC_SPN | _AdminConsole/node01/InfaDomain@COMPANY.COM |
httpuser01 | NODE_HTTP_SPN | HTTP/US001DEV.company.com@COMPANY.COM |
MRSdevuser01 | SERVICE_PROCESS_SPN | MRS_dev/node01/InfaDomain@COMPANY.COM |
DISdevuser01 | SERVICE_PROCESS_SPN | DIS_dev/node01/InfaDomain@COMPANY.COM |
nodeuser02 | NODE_SPN | isp/node02/InfaDomain/COMPANY.COM |
admintooluser02 | NODE_AC_SPN | _AdminConsole/node02/InfaDomain@COMPANY.COM |
httpuser02 | NODE_HTTP_SPN | HTTP/US005DEV.company.com@COMPANY.COM |
CATdevuser01 | SERVICE_PROCESS_SPN | CAT_dev/node02/InfaDomain@COMPANY.COM |
You also create a keytab for the LDAP bind user account that is used to access and search Active Directory during LDAP synchronization.
1. Create a keytab file for the Kerberos principal user account that you created for each node in Active Directory.
Copy the file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a Kerberos principal user account named nodeuser01:
ktpass.exe -out node01.keytab -princ isp/node01/InfaDomain/COMPANY.COM -mapuser nodeuser01 -crypto all -ptype KRB5_NT_PRINCIPAL
2. Create a keytab file for each HTTP process Kerberos principal user account that you created.
If the domain uses Kerberos cross realm authentication, the principal user account can exist in any Kerberos realm the domain uses.
Copy the file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a Kerberos principal user account named httpuser01:
ktpass.exe -out webapp_http.keytab -princ HTTP/US001DEV.company.com@COMPANY.COM -mapuser httpuser01 -crypto all -ptype KRB5_NT_PRINCIPAL
3. Create a keytab file for each Administrator tool Kerberos principal user account that you created.
Copy the file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a Kerberos principal user account named admintooluser01:
ktpass.exe -out _AdminConsole.keytab -princ _AdminConsole/node01/InfaDomain@COMPANY.COM -mapuser admintooluser01 -crypto all -ptype KRB5_NT_PRINCIPAL
4. Create a keytab file for each Informatica application service Kerberos principal user account that you created.
Copy the file name from the KEY_TAB_NAME column in the SPNKeytabFormat.txt file. Copy the service principal name from the SPN column in the SPNKeytabFormat.txt file.
The following example creates a keytab file for a service Kerberos principal user account named MRSdevuser01:
ktpass.exe -out MRS_dev.keytab -princ HTTP/US001DEV.company.com@COMPANY.COM -mapuser MRSdevuser01 -crypto all -ptype KRB5_NT_PRINCIPAL
5. Create a keytab for the LDAP bind user account that is used to access and search Active Directory during LDAP synchronization.
Structure the value for the -princ option as <principal name>@<KERBEROS REALM>. Include the name of the LDAP configuration for the Active Directory server in the keytab file name. Structure the keytab file name as follows: <Active Directory LDAP configuration_name>.keytab.
The following example creates a keytab file for a service principal user account named ldapuser:
ktpass.exe -out ActiveDirectoryServer1.keytab -princ ldapuser@COMPANY.COM -mapuser ldapuser -crypto all -ptype KRB5_NT_PRINCIPAL
Verify the Service Principal Names and Keytab Files
You can use Kerberos utilities to verify that the SPNs and the keytab files are valid. You can also use the utilities to determine the status of the Kerberos Key Distribution Center (KDC).
You can use Kerberos utilities such as kinit and klist to view and verify the SPNs and keytab files. To use the utilities, ensure that the KRB5_CONFIG environment variable contains the path and file name of the Kerberos configuration file. For more information about running the Kerberos utilities, see the Kerberos documentation.
Use the following utilities to verify the SPNs and keytab files:
- kinit
You can use the kinit utility to request a ticket-granting ticket (TGT) from the KDC and verify that a keytab file can be used to establish a Kerberos connection. If the keytab and specified SPN are valid, the command obtains a ticket, and then caches the ticket in the specified cache.
The kinit utility is available in the following directory on an Informatica node:
<Informatica installation directory>\java\jre\bin
- To request a ticket-granting ticket for an SPN, run the following command:
kinit -c <cache name> -k -t <keytab file name> <service principal name>
- The following output example shows the ticket-granting ticket created in the default cache for a specified keytab file and SPN:
Cache: \temp\krb
Using principal: isp/node01/InfaDomain/COMPANY.COM
Using keytab: node01.keytab
Authenticated to Kerberos v5
- klist
- You can use the klist utility to list the Kerberos principals and keys in a keytab file. To list the keys in the keytab file and the time stamp for the keytab entry, run the following command:
klist -k -t <keytab file name>
- The following output example shows the principals in a keytab file:
Keytab name: FILE:node01.keytab
KVNO Timestamp Principal
---- ----------------- --------------------------------------------------------
3 12/31/16 19:00:00 MRS_dev/node01/InfaDomain@COMPANY.COM
3 12/31/16 19:00:00 MRS_dev/node01/InfaDomain@COMPANY.COM
3 12/31/16 19:00:00 MRS_dev/node01/InfaDomain@COMPANY.COM
3 12/31/16 19:00:00 MRS_dev/node01/InfaDomain@COMPANY.COM