Perform the following tasks if your Axon license expires:
- Verify that the PostgreSQL Database Service is Running
- Replace Your Axon License Key
- 1. Contact Informatica Global Customer Support to obtain a new license key.
- 2. In the Linux environment, replace the expired license key file with the new license key file in the following directory:
To verify that the PostgreSQL database service is running, go to the <INSTALLATION_DIR>/axonhome/third-party-app/scripts directory in the Linux environment, and run the following command:
sh postgresql status
If the service is shut down, go to the <INSTALLATION_DIR>/bin directory, and run the following command to restart the Axon services:
sh startup.sh
Note: Use the same commands to verify that the database services is running for the PostgreSQL database deployed on a different node and external nodes, such Amazon RDS and Microsoft Azure Database for PostgreSQL.
To replace your Axon license key, perform the following steps:
<INSTALLATION_DIR>/axonhome/axon/
Make sure that the new license key file and expired license key file share the same name.
Note: When you clear the cache and restart the Axon services, the Axon web interface might be disrupted for some users that are logged into Axon. Informatica recommends that you update the cache after you save your changes in all the System Settings pages. Additionally, perform this action during a maintenance period when very few users are using Axon.
If users cannot log in to Axon using SSO, perform the following tasks:
- Verify the SSO Settings
- 1. In the IDP, make sure that Axon is configured as a SAML 2.0 application.
- 2. In the IDP, make sure that Axon details and the properties for the SAML attributes are entered correctly.
- 3. If you cannot access the SSO settings in Axon, disable SSO from the Linux environment.
- a. Run the following command to define the Axon environment variable so that the Linux system can access the Axon resources at the correct location:
- b. Go to the <INSTALLATION_DIR>/axonhome/axon directory, and run the following command to disable SSO:
- 4. In Axon, make sure that the values of the SAML metadata are entered correctly.
- Verify the SSO Settings in the SAML Response File
Make sure that you have configured the SSO settings correctly. For SSO configurations, refer to Configure Single Sign-On.
source <INSTALLATION_DIR>/scripts/exportEnv.sh
<INSTALLATION_DIR>/axonhome/third-party-app/php/bin/php bin/console informatica:sso-disable
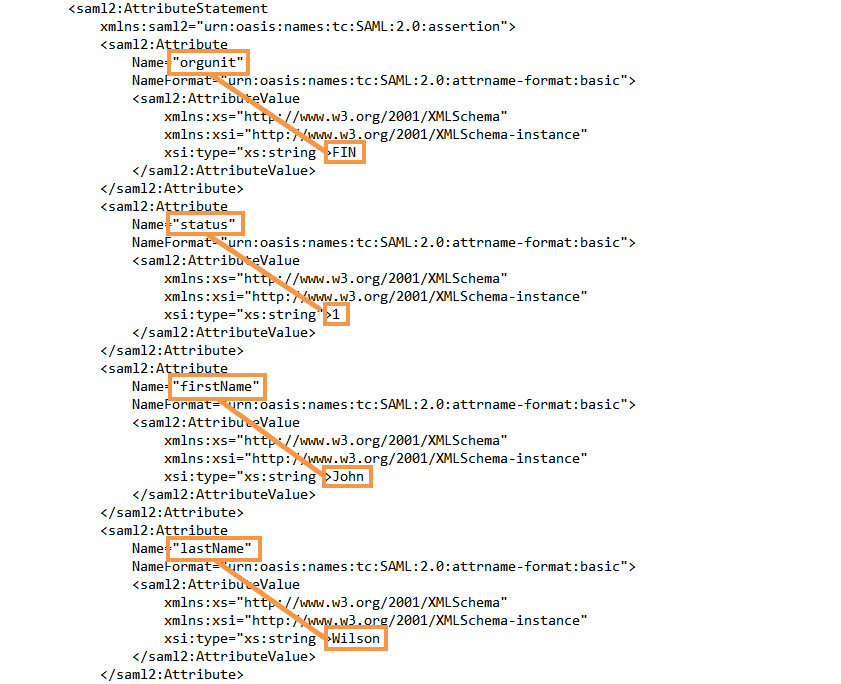
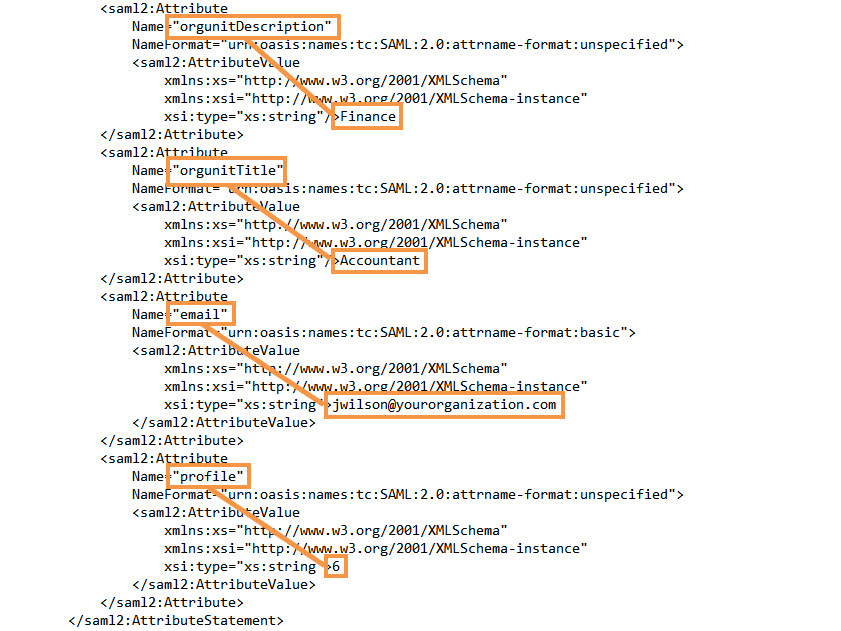
After Axon users enter their SSO credentials, the IDP sends a SAML response to Axon. Open the response file and verify that the following properties display the correct values for the Axon users:
Property | Value |
|---|---|
orgunit | Organization unit of the Axon user |
statusID | Status of the Axon user in the IDP database. The value must be 1. |
firstName | First name of the Axon user |
lastName | Last name of the Axon user |
orgunitDescription | Organization unit description for the Axon user |
orgunitTitle | Title of the Axon user in the organization unit |
email | Email address of the Axon user |
profile | Profile of the user in Axon. The value must be 4, 5 or 6. |
For example, the values for the Axon user John Wilson might look like this:
Verify that the X.509 certificate values are correctly retrieved from the IDP. For example, the X.509 certificate value might look like this:
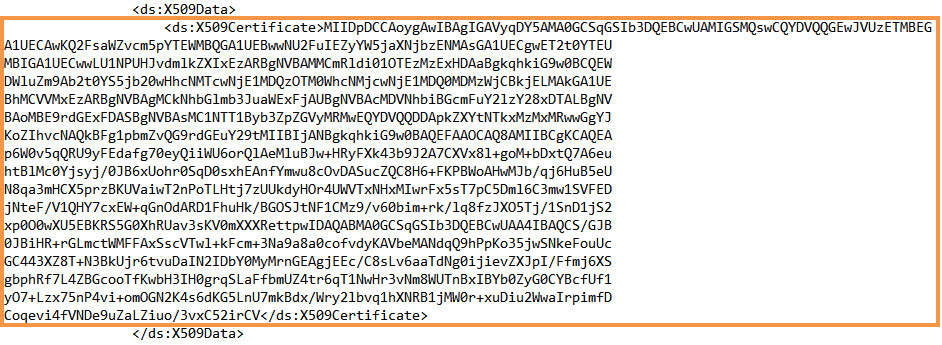
If you have configured the properties in the IDP correctly, the values in the SAML response file must match the values you enter in the IDP.