Administration of Microsoft Sharepoint Online Connector
Before you use Microsoft Sharepoint Online Connector, you must generate the client ID, client secret, bearer realm, authorization code, and refresh token that are required to establish a Microsoft Sharepoint Online connection.
To generate the client ID and client secret, create a Microsoft Sharepoint Online account to access the Microsoft Sharepoint Online application. You must enable the Google PostMan application plug-in to generate the bearer realm, authorization code, and refresh token in the Google PostMan application.
Complete the following prerequisite tasks:
- 1. Generate the client ID and client secret.
- 2. Generate the bearer realm of your site.
- 3. Generate the authorization code.
- 4. Generate the refresh token.
Generate the Client ID and Client Secret
The client ID and client secret are required to generate a valid access token.
Perform the following steps to generate the client ID and client secret:
1. Log in to the Microsoft Sharepoint Online account.
2. Enter the following site or subsite URL:
Site: https://<sitename.com>/_layouts/15/appregnew.aspx
Subsite: https://<sitename.com>/<subsitedomain>/_layouts/15/appregnew.aspx
The App Information page appears.
3. Click Generate next to the Client Id field.
The value of the client ID is displayed in the
Client Id field. The following image shows the
App Information page where you can generate the values of the client ID and client secret:
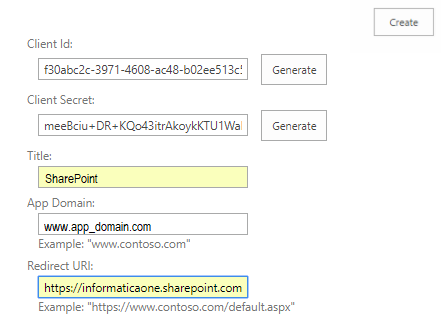
4. Click Generate next to the Client Secret field.
The value of the client secret is displayed in the Client Secret field.
5. Enter an appropriate title for the App in the Title field.
6. Enter an app domain name in the App Domain field.
For example, www.google.com
7. Enter a URL in the Redirect URL field.
For example, https://localhost/. You must enter the same redirect URL in the connection property.
8. Click Create.
The page redirects to the Microsoft Sharepoint Online page and the following message appears:
The app identifier has been successfully created.
The values of the client Id, client secret, title, and redirect URL are displayed.
Generate the Bearer Realm
A bearer realm is a unique ID provided for each user. You must generate the bearer realm to obtain the authorization code.
Perform the following steps to generate the bearer realm:
1. Open the Google PostMan application.
2. Enter the following site or subsite URL in the Google PostMan application:
Site: https://<sitename.com>/_layouts/15/appregnew.aspx
Subsite: https://<sitename.com>/<subsitedomain>/_layouts/15/appregnew.aspx
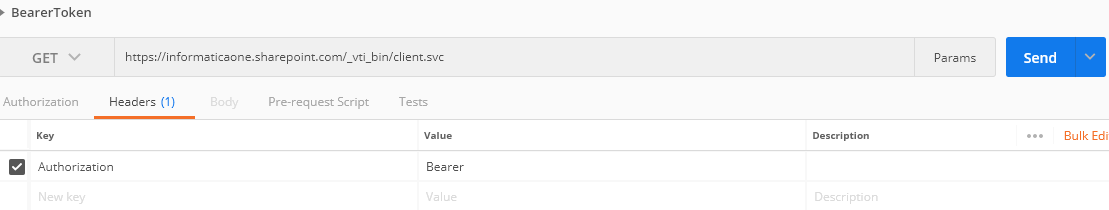
The following image shows the BearerToken page where you can generate the value of the bearer realm:
3. Select the GET method.
4. On the Headers tab, enter Authorization in the Key field and Bearer in the Value field.
5. Click Send.
6. Select the Headers tab in the Response header.
The bearer realm value appears in the WWW-Authenticate section. For example:
Bearer realm="77baf95d-f3e0-42b-aa08-9b798b8c177b"
Generate the Authorization Code
You must generate the authorization code to gain access to the current site and to generate a valid refresh token.
Perform the following steps to generate the authorization code:
1. Enter the following site or subsite URL in the Google chrome browser:
Site: https://<site.sharepoint.com>/_layouts/15/OAuthAuthorize.aspx?client_id=<client_GUID>&scope=<app_permissions_list>&response_type=code&redirect_uri=<redirect_uri>
For example, https://icloudconnectivitydev.sharepoint.com/_layouts/15/oauthauthorize.aspx?client_id=ecea5b1b-80e4-4f3e-a269-48b85c1797a8&scope=Web.Manage&response_type=code&redirect_uri=https%3A%2F%2Flocalhost%2F
Subsite: https://<site.sharepoint.com>/<subsitedomain>/_layouts/15/OAuthAuthorize.aspx?client_id=<client_GUID>&scope=<app_permissions_list>&response_type=code&redirect_uri=<redirect_uri>
For example, //informaticaone.sharepoint.com/sites/TEST/_layouts/15/oauthauthorize.aspx?client_id=ecea5b1b-80e4-4f3e-a269-48b85c1797a8&scope=Web.Manage&response_type=code&redirect_uri=https%3A%2F%2Flocalhost%2F
2. Click Trust it to grant the application read access to the current site after the page redirects to the redirect URL page that you specify in the connection property.
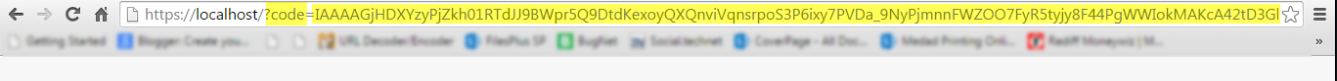
The redirect URL page includes the authorization code as a query string in the following format:
https://<redirect_url>/?code=<authcode>
The following image shows the authorization code as a query string in the URI:
Generate the Refresh Token
A refresh token is required to perform the POST and GET methods in the Google PostMan application. After you generate a refresh token, it is valid for six months.
Perform the following steps to generate the refresh token:
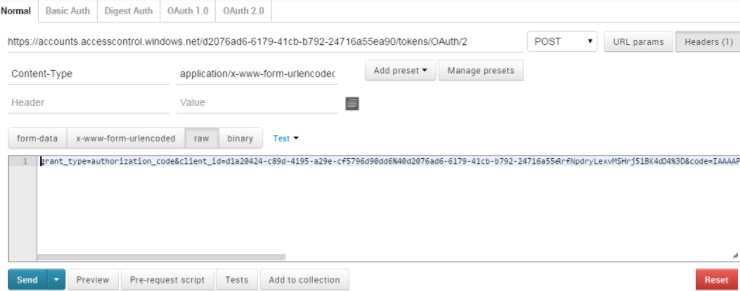
1. Enter the following URL in the Google PostMan application:https://accounts.accesscontrol.windows.net/<bearer_realm>/tokens/OAuth/2
The following image shows the Normal tab in the Google PostMan application where you can configure the properties to generate the refresh token:
2. Select the POST method.
3. On the Header tab, enter Content-Type in the Key Name field and application/x-www-form-urlencoded in the Value field.
4. On the Body tab, enter the xml request in the following format:
grant_type=authorization_code &client_id=<client_id>@<bearer_realm> &client_secret=<client_secret> &code=<auth_code> &redirect_uri=<redirect_url> &resource=< audience principal ID >/<site_host>@<bearer_realm>
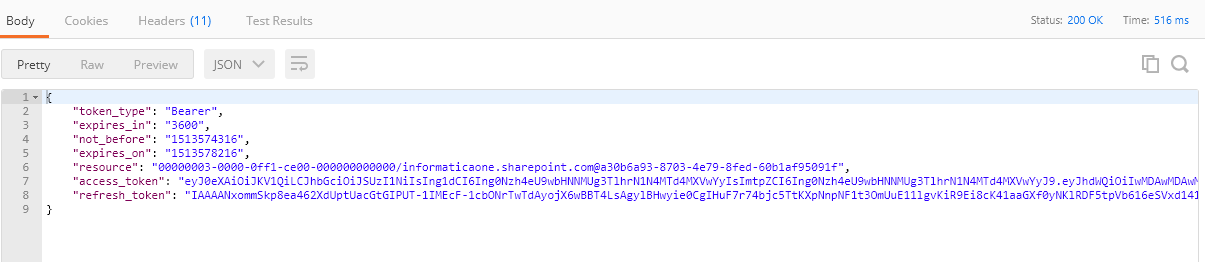
5. Click Send.
The refresh token is generated in the Response tab. The following image shows the Response tab where the refresh token is generated: