Media Manager and Supplier Portal Integration
Prerequisite
Before you can start with this chapter, you need to have finished the following parts:
Setup Hotfolder
We have to define a hotfolder in the native Hotfolder client. This hotfolder is monitoring a defined folder and import the found assets to the Product 360 - Media Manager.
Start "administrations mode" of the Hotfolder module.
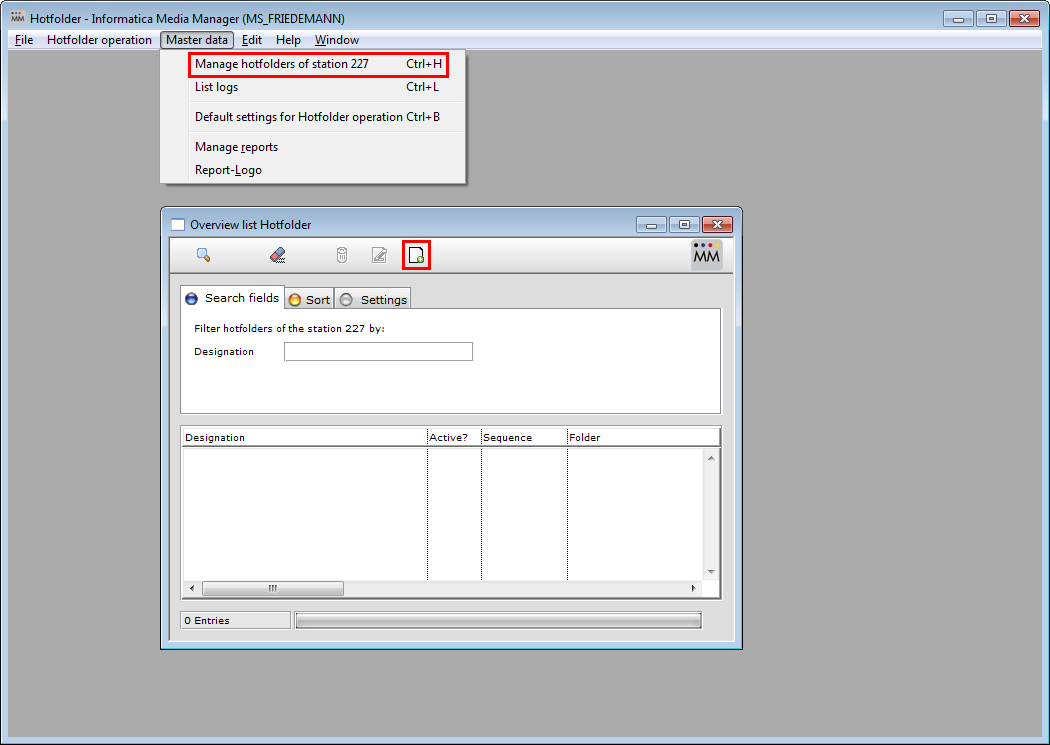
Choose "Manage hotfolder of station XX" and create a new Hotfolder defintion.
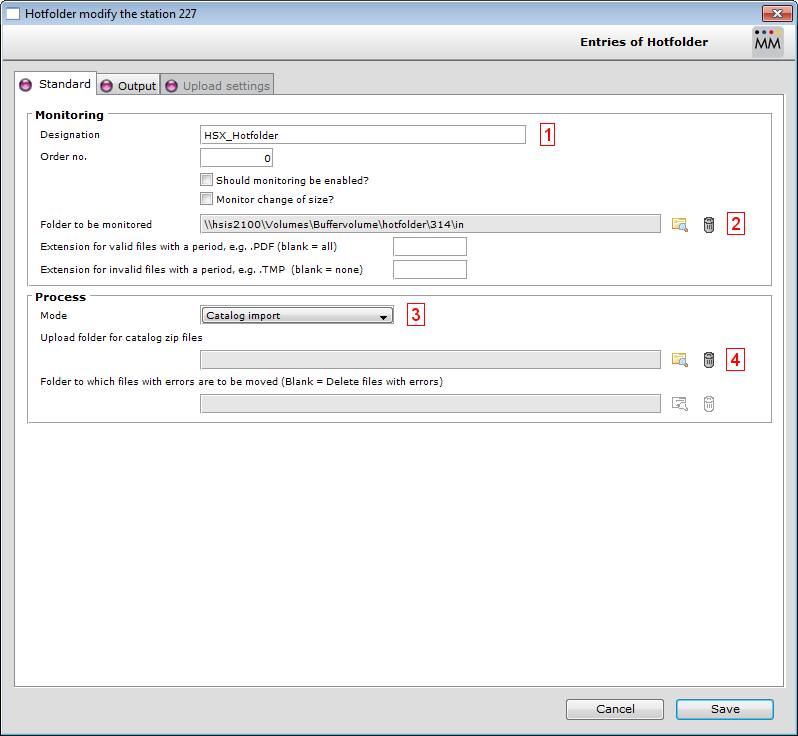
Settings at the Standard panel:
#1: Define a name for the Hotfolder
#2: Select a folder to be monitored.
#3: Define mode "Catalog import".
#4: Choose a target folder for the uncompressed uploads
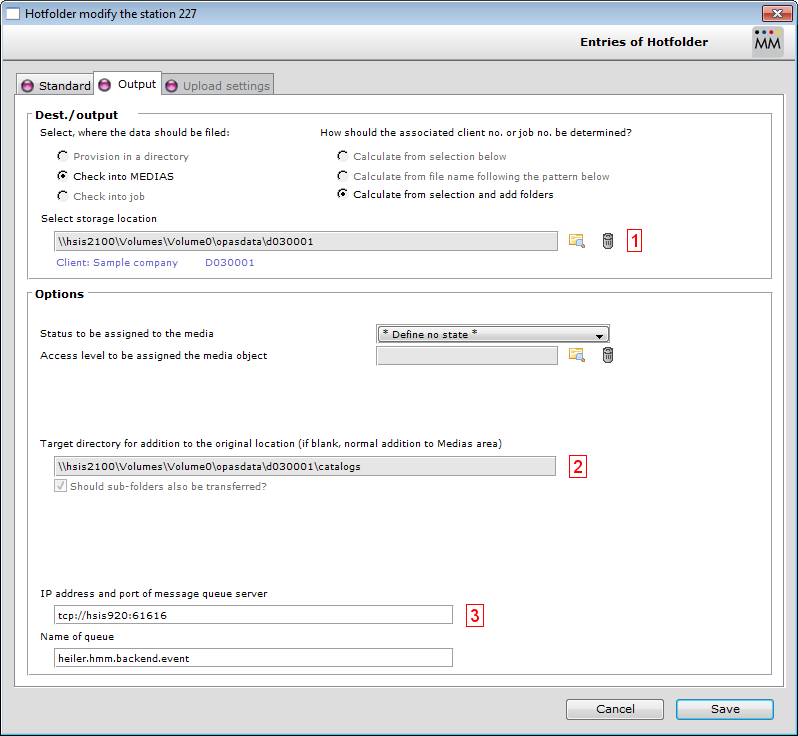
Additional settings are defined at the "Output" panel.
#1: Choose a customer. This customer has to be defined be the REST service configuration.
#2: Check if the folder exists. If not create the "catalogs" folder.
#3: Define the location of your ActiveMQ and enter the name of the queue. Default name is "heiler.hmm.backend.event".
The configuration is done now. Save your settings ...
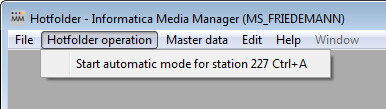
... and start the Hotfolder.
Setup REST Service
Now we have to setup the REST service to upload the asset containing archives. Due to performance reasons we recommended to use different machines for the REST service and the Hotfolder.
Tomcat and Java
It is recommended to use the Tomcat included in the OpasGWebserver.zip of the Media Manager Web application.
Installation HMM REST war
Add the HMM REST war to the tomcat by copying the rest.war file to Tomcat/webapps/ folder.
Configuration HMM REST war
The REST service has to be configured. The config files can be found at Tomcat/webapps/rest/WEB-INF/classes/META-INF/spring
Database configuration
Configure your HMM database at the file hmm-database.properties. This connection is the same connection used by the native HMM modules. A connection could look like this:
database.type=oracle
database.url=jdbc:oracle:thin:@hsis300:1521:hmm
database.username=opasuser
database.password=OPASPASS
database.driverClassName=oracle.jdbc.driver.OracleDriver
Additional configuration
Configure the HMM customer in the config file hmm-inbox.properties . The customer number has to be defined at the key hmm.inbox.standardOrganisation
Encrypted passwords in configuration files (since 8.0.6.01)
Product 360 Media Manager Web supports the encryption of secure information like passwords in the configuration files. The encryption will be executed only if your secure information in the configuration files is enclosed by the marker [_to_encrypt_].
So, if you want to have e.g. the password "Password" encrypted in a configuration file just use the marker before and after the password like this: [_to_encrypt_]Password[_to_encrypt_]. Please note first encryption gets done with the start of the Tomcat.
For example in hmm-database.properties:
database.type=mssqldatabase.url=jdbc:sqlserver://host:1433;DatabaseName=dbnamedatabase.username=userdatabase.password=[_to_encrypt_]Password[_to_encrypt_]database.driverClassName=com.microsoft.sqlserver.jdbc.SQLServerDriverUsage of strong cryptographic algorithms to encrypt/decrypt secure information
Due to import control restrictions of some countries, the version of the JCE policy files that are bundled in the Java 8 Runtime Environment allow "strong" but limited cryptography to be used. This means if you want to use a strong cryptographic algorithm like AES-256 you will need to replace your Java Runtime's JCE policy files in the OpasGWebServer\java\jre\lib\security folder. Otherwise you will run into errors during encryption/decryption in Product 360 Media Manager Web, saying you're using an illegal key size.
Also after update to newest Hotfix the Java JCE policy files must be replaced in corresponding OpasGWebServer\java\jre\lib\security folder.
See also http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
Usage of AES-256 cryptographic algorithm to encrypt/decrypt secure information
Product 360 Media Manager Rest Service provides a default implementation for the encryption of secure information with an internal and securely stored Key using AES-256.
For sophisticated deployments we recommend to integrate with Encryption Key Management solutions like Amazon AWS or Azure KeyVault and use the API we offer to send and receive data for encryption to these key stores securely.
Startup
Start your Tomcat. The default URL of the REST service is
YOUR_MASCHINE:YOUR_TOMCAT_PORT/rest/rest
Check HSX Functions and Installation for additional information about the existing REST calls.