Configure Single Sign-On
When you enable Single Sign-On (SSO), users can log in to Axon using login credentials that are common to other applications in your organization. Axon uses SSO to authenticate users based on the Identity Provider (IDP) credentials.
To enable SSO, you must configure Axon as an application in the IDP tool. Axon supports any IDP that uses SAML 2.0 authentication.
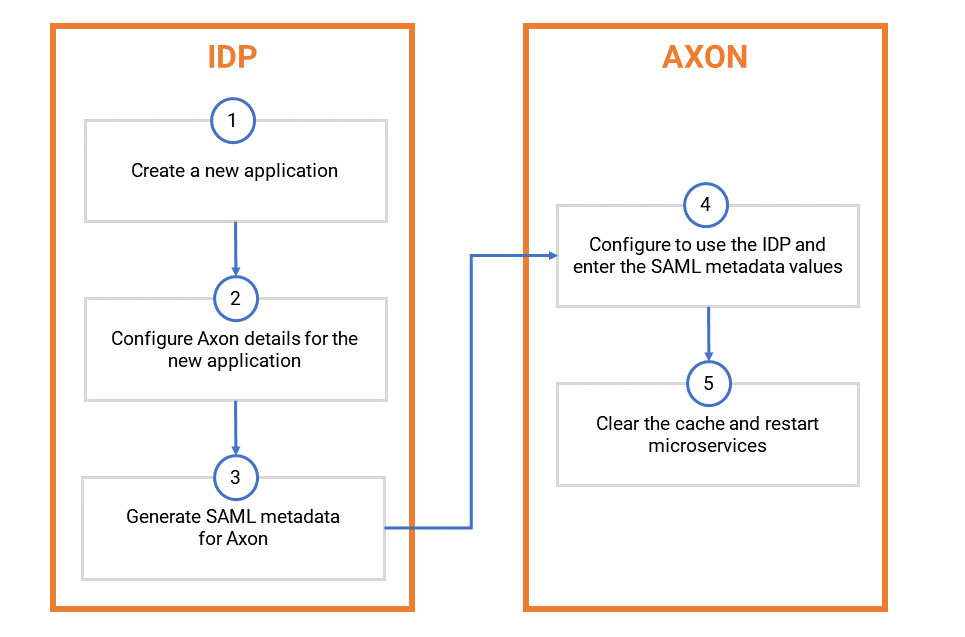
The steps to configure SSO for Axon are shown in the following diagram:
Note: If you configure Axon to access the LDAP server and in addition use SSO to authenticate the users, the SSO authentication takes precedence. When Axon users attempt to log in, the browser displays the login window of the IDP. To configure Axon to access the LDAP directory, refer to
Retrieve Users from LDAP Directory to Axon.
Create a New Application in the IDP
You must first add Axon as an application in the IDP.
1. Log in to the IDP configuration page and choose to add a new SAML 2.0 application.
2. Enter the new application name as Axon.
Configure Axon Details for the New Application in the IDP
To configure Axon in the IDP, perform the following tasks:
1. Set the name ID format and user name format of users to Email. This step makes sure that the IDP expects the Axon user's name ID and user name in the format of an email address
2. Set the SSO domain URL to http(s)://<Axon_host>:<9999_or_9443_or_custom_port_number>/saml/acs. This URL is the endpoint for SSO login to Axon.
3. Set the audience URL to http(s)://<Axon_host>:<9999_or_9443_or_custom_port_number>/saml/metadata. This URL is the service provider metadata that is obtained from Axon.
4. Set the following mandatory properties for the SAML attributes:
Property | Value |
|---|
firstName | First name of the Axon user |
lastName | Last name of the Axon user |
email | Email address of the Axon user |
Note: Make sure that the SAML attribute properties are configured for every Axon user in your organization. If a property is not configured, you must add the property to the IDP and enter valid values of the property for each Axon user.
5. You can set the following optional properties for the SAML attributes:
Property | Value |
|---|
orgunit | Organization unit of the Axon user |
orgunitTitle | orgunitTitle |
orgunitDescription | Description of the Axon user's organization. Note: If you do not select the orgunitDescription property, or if you select the orgunitDescription property and do not assign a default value, Axon assigns a blank value to all organization units. |
statusID | Status of the Axon user in the IDP database. Set the value to 1. Note: If you do not select the statusID property, or if you select the statusID property and do not assign a default value, Axon assigns the Active value to all the users. |
profile | Profile of the user in Axon. Enter one of the following values: - - Enter 4 for a WebUser profile.
- - Enter 5 for an Admin profile.
- - Enter 6 for a SuperAdmin profile.
If you do not enter a value for the field, Axon assigns the WebUser profile to the user. If you enter a value other than 4, 5 or 6, the user account is not created, and the user cannot log in to Axon. |
Note: When you configure Axon to use SSO authentication, you can assign a default organization unit for all Axon users. If you choose to assign a default organization unit, the
orgunit,
orgunitTitle, and
orgunitDescription properties are optional. To configure Axon to use SSO authentication, refer to
Configure Axon and Enter the SAML Metadata Values.
6. In the IDP, provide access to the new Axon application to all Axon users and user groups.
The Axon installer assigns the following port numbers as the default value for the Apache server:
- •If you use HTTP authentication, the installer assigns 9999 as the default port number for the Apache server.
- •If you use HTTPS authentication, the installer assigns 9443 as the default port number for the Apache server.
You can enter a custom port number for the Apache server instead of choosing the default value.
Depending on whether you selected the default port number or entered a custom port number for the Apache server during Axon installation, you must enter the correct port number in the SSO domain URL and audience URL fields.
Generate a SAML Metadata for Axon in the IDP
After you have configured Axon in the IDP, you must obtain the SAML metadata. The SAML metadata is used when you configure Axon to use the IDP.
The SAML metadata contains the following properties:
- •Identity Provider Endpoint
- •SSO Entity ID
- •X.509 Certificate
Make a note of the values of these properties. You must enter these values when you configure Axon.
Note: The SAML metadata is based on the configuration parameters that you have entered in the IDP. If you modify any of the parameters in the IDP, you must generate new SAML metadata values.
Configure Axon and Enter the SAML Metadata Values
Perform the following steps to configure Axon to use SSO:
You must have the Super Admin profile to perform this task.
1. From the Axon toolbar, click the Admin Panel menu item under your user name.
2. In the menu on the left, under the Customize & Configure category, click System Settings.
3. In the Group list, select SAML Configuration.
4. Click Edit.
5. Set the following properties for the IDP:
Property | Description |
|---|
SSO URL | Enter http(s)://<Axon_host>:<9999_or_9443_or_custom_port_number>/saml/login. This URL redirects the user from the Axon login page to the SSO login page. Note: The default port number for HTTP authentication is 9999, and the default port number for HTTPS authentication is 9443. |
Require SSO Authentication | Restrict guest users from viewing Axon objects. If you select the check box, guest users in Axon cannot view objects when they click Search on the toolbar. They must log in to Axon to browse and view Axon objects. If you clear the check box, guest users can view Axon objects when they click Search on the toolbar. |
SSO Default Org Unit | Enter the reference number of the default organization unit that Axon assigns to all users. |
IDP Endpoint | Enter the value that you noted in the SAML assertion. |
IDP Entity ID | Enter the value that you noted in the SAML assertion. |
IDP X.509 Certificate | Enter the value that you noted in the SAML assertion. Note: Enter this value in a single line without any line breaks. |
6. Click Save.
Clear the Axon Cache and Restart Services
After you have configured Axon in the identity management tool and configured the Axon SAML files, you must update the Axon cache with the new configuration values.
In the Linux environment, run the following command to clear the Axon cache and restart the necessary services:
sh <INSTALLATION_DIR>/axonhome/third-party-app/scripts/paramsync
When you run the paramsync script, Axon restarts the HTTPD, Memcached, and email notification services.