Web Configuration
Activate Product 360 - Web Permissions & Interface Visibility
Product 360 - Web contributes some action rights and interface visibility elements which allow customization of the Web User Interface. To change these permissions, open the Product 360 - Desktop Organization perspective. A couple of web-specific actions rights are shown in the group "Web permissions" in the Action Rights View.
Even more configuration options are available on the Interface Visibility Tab. Please note that all web specific elements are only shown after the Web application was loaded at least once in the Browser.
The shown elements are dynamic and depend on the concrete configuration of the system. Hence new list definition contributions can be assigned to different user groups on the fly.

For some visibilities it it not enough to just activate them in the Interface visibility tab. The appropriate action right for general access needs also to be activated.
For example to see the Quality status tab for items in the web ui it is not enough to activate "Tab visibility: Item, Quality Status", also the Action right "Quality status, general access" needs to be activated
Product 360 - Web Specific Configuration
All configuration for Product 360 - Web is done in <PIM_SERVER_INSTALLATION_ROOT>/server/configuration/HPM/webfrontend.properties. This is a complete list of all configuration parameters:
|
|
|
|
web.client.default.language
|
Default language, effects login page only, other things are shown in selected on
Default: eng |
|
web.client.default.locale
|
Default locale, effects login page only, other things are shown in
Default: en_US |
|
web.client.available.locales
|
List of all available locales for login form. Must be a subset of language Default value for this setting is a list of all languages where an official i18n package is available for. Default: de_DE,en_US,fr_FR,ru_RU,nl_NL,sv_SE,fi_FI, |
|
web.client.theme |
Theme affects the application appearance. Default: symphony |
|
web.client.httpSession.timeout |
Session time-out in seconds. Default (28800 seconds equals 8 hours): 28800 |
|
web.client.xframeoptions |
If set, an X-Frame-Options response header will be set in the main page http response |
|
web.client.headers.response
|
It is possible add http response headers to each http response send to the client. This applies for all http resources below /pim context. web.client.headers.response.Strict-Transport-Security = max-age=31536000; includeSubDomains Default: not specified |
|
web.client.headers.response.Content-Security-Policy
|
This is to apply the appropriate Content-Security-Policy header to the http response send to client. The default value is * as this property varies from one environment to other,this property can be changed to appropriate value based on the environment. To know how to change the value please refer to https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy. Default: * |
|
web.client.detailform.inputs.limit |
Maximum number of inputs at detail form displayed by default. If inputs count limit will be reached, Default: 30 |
|
web.client.filter.minimum.length |
Minimum length for text field used for filtering list views. Value has to be >= 0. Default: 1 |
|
web.client.text.filter.timeout |
Timeout for text filters. It set a time for response between entered letter and search results. Default: 200 |
|
web.client.clone.referencetype.Article |
Reference type between cloned element and original. Value is based on repository Enum.ArticleReferenceType keys. Default: "" |
|
web.definition.dir |
Relative path to web definitions XML files, starting from configuration directory. By default points to configuration/server/webdefinitions Default: /webdefinitions |
|
web.client.default.fetch.size |
Default number of rows that are fetched in master list views. Smaller numbers result in slightly faster loading times, Default: 200 |
|
|
|
|
web.client.mediaasset.servlet.path |
Media asset bridge servlet (root path).. Default: /pim/mediaasset |
|
web.client.mediaasset.prefered.quality |
Prefered quality for thumbnails at mediaasset viewer. Default web |
|
web.client.mediaasset.thumbnail.detail.panel.type |
Detail form top image type from available mediaasset. Default normal |
|
web.client.mediaasset.list.thumb.small |
Documents list view thumbnails quality mapping for small images. Default: small |
|
web.client.mediaasset.list.thumb.normal |
Documents list view thumbnails quality mapping for standard images. Default: normal |
|
web.client.mediaasset.list.thumb.big |
Documents list view thumbnails quality mapping for large images. Default: big |
|
web.client.mediaasset.list.page.size |
Number of multimeda document that are display on a single page. Default: 25 |
|
|
|
|
web.client.hsx.supplier.login |
Login name of Product Manager user that is used for supplier editor. Default: supplier |
|
web.client.hsx.supplier.password |
Login password of Product Manager user that is used for supplier editor. Default: supplier If you want to encrypt the password please refer to chapter Encryption of secure information in the Server Installation manual. |
|
web.client.hsx.readonly.supplier.login |
Login name of Product Manager user that is used for supplier read-only view. Default: readonlysupplier |
|
web.client.hsx.readonly.supplier.password |
Login password of Product Manager user that is used for supplier read-only view. Default: readonlysupplier If you want to encrypt the password please refer to chapter Encryption of secure information in the Server Installation manual. |
|
|
|
|
web.client.hps.max.display.facet |
Maximum number of displayed search facets. Default: 5 |
|
|
|
|
web.client.export.max.selection |
Maximum number of records that can be exported from the Web UI. Default: 200 |
|
|
|
|
web.client.ui.search.and.replace.dialog.default.action |
The default action in the Search and Replace dialog. Available values: SEARCH_AND_REPLACE, SET Default: SEARCH_AND_REPLACE |
|
web.client.ui.classification.dialog.default.type |
The default classification type in the Classification dialog. Available values: MOVE, COPY Default: MOVE |
|
web.client.ui.show.transition.fields.content |
Show content of transition fields in the Field Selection dialog or not. Available values: TRUE, FALSE Default: TRUE |
|
web.client.autoload.catalog |
Autoselect Master catalog or catalog stored in cookies after login. Possible values: true, false The default is: true |
|
web.client.menu.initial.structure |
Specifies external identifier for structure which will be initially selected in context. If not specified - value from com.heiler.ppm.structure.server/primaryStructureIdentifier will be used. First available value will be used if none of the properties mentioned above specify explicit value. |
|
web.client.popup.initial.structure |
Specifies external identifier for structure which will be initially selected in classification popup. If not specified - first available value will be used. |
|
web.client.enum.sort.locale-sensitive
|
Specifies whether to use locale-sensitive (= "true") resp. locale-insensitive (= "false") string comparison in enum list and lookup value sorting. Possible values: true, false The default is: false |
|
web.client.enum.sort.case-sensitive
|
Specifies whether to use case-sensitive (= "true") resp. case-insensitive (= "false") string comparison in enum list and lookup value sorting. Possible values: true, false If web.client.enum.sort.locale-sensitive is "true" this property will be ignored The default is: false |
|
|
|
|
web.vaadin.productionMode |
Enables the application in development mode, must be true in production. Default: true |
|
web.vaadin.disable-xsrf-protection |
Enables the Vaadin XSRF protection. Set to true when running automated web tests. Default: false |
|
web.vaadin.widgetset |
Vaadin Widgetset which is used in application. Default: com.heiler.ppm.web.widgetset.Widgetset |
|
web.vaadin.heartbeatInterval |
UI Heartbeat interval to track open sessions. Default value is 300 seconds (5 minutes). |
|
web.vaadin.closeIdleSessions |
Close http session after user inactivity. Default: true |
|
web.vaadin.pushMode |
Mode for server side push. Possible values: AUTOMATIC, MANUAL, DISABLED Default: AUTOMATIC |
|
web.vaadin.pushTransport |
Transport mode for server side push. Possible values: WEBSOCKET, STREAMING, LONG_POLLING. Default: STREAMING |
Setup HTTPS/SSL Security
When configuring Product 360 Web for production usage, setting up https security is mandatory. Otherwise all user credentials will be send as plain text through the internet. There are two scenarios, how security can be ensured:
Setup a Reverse Proxy that transparently forwards all requests to the Product 360 Application Server. SSL certificates are installed on the Reverse Proxy.
Install SSL certificates directly on Product 360 Application Server.
A combination of both is possible, too.
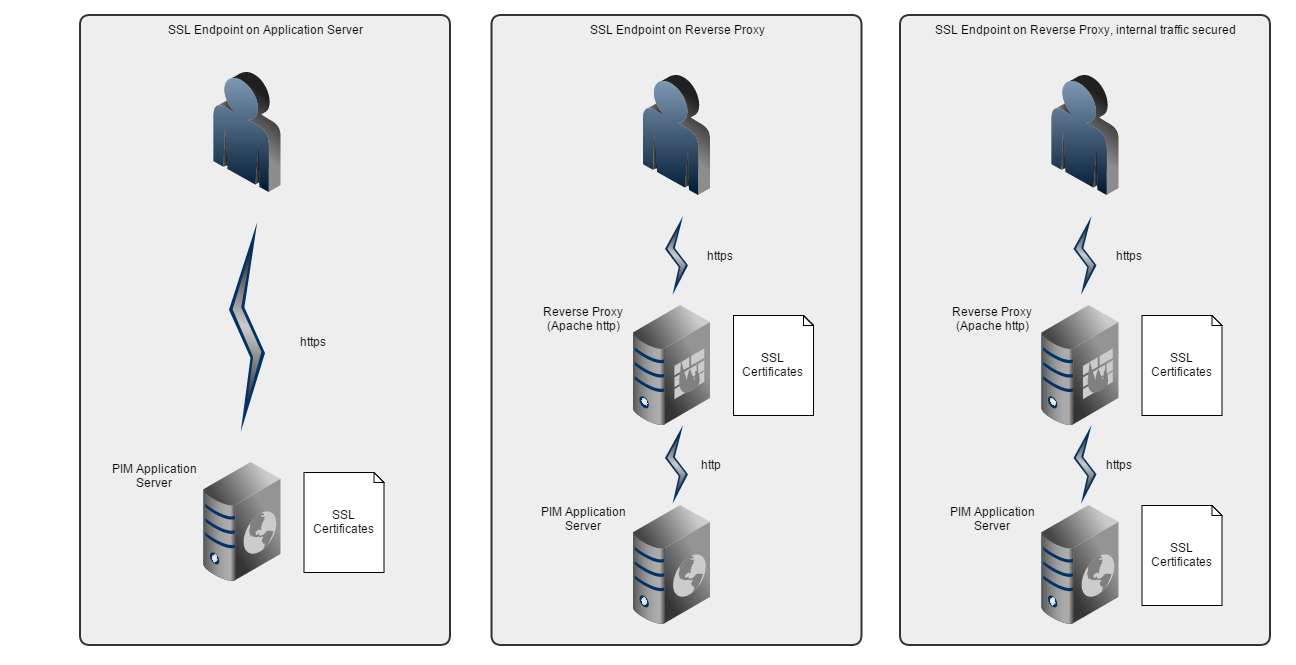
Running Product 360 - Web behind a Reverse Proxy
For SSL support and security reasons, customers typically run web applications behind a dedicated web server (called reverse proxy) which transparently handles all incoming requests from clients and forwards them to the Product 360 -Web application server.
Please expose only the dedicated P360 interface you want to use externally.
If the P360 web application should be used expose only http://<hpmserver>:<hpmport>/pim to the public.
Never expose all endpoints running at http://<hpmserver>:<hpmport>.
Product 360 - Web supports this scenario and has been tested with Apache 2.2. If you have installed and configured the Apache, the following lines in httpd.conf are necessary for request forwarding:
# Load the needed mod_proxy modulesLoadModule proxy_module modules/mod_proxy.soLoadModule proxy_connect_module modules/mod_proxy_connect.soLoadModule proxy_http_module modules/mod_proxy_http.so#Reverse ProxyProxyPass /pim http://<hpmserver>:<hpmport>/pimProxyPassReverse /pim http://<hpmserver>:<hpmport>/pimFor setup of SSL, please refer to the corresponding Apache manuals. For a guide how to export a certificate or private key from the Java keystore into an Apache Webserver compatible format, please check this page at http://security.stackexchange.com/questions/3779/how-can-i-export-my-private-key-from-a-java-keytool-keystore .
An example configuration for setting up a Reverse Proxy together with a Virtual Host for https looks like this:
<VirtualHost _default_:443> ProxyPass "/pim" "http://localhost:1512/pim" ProxyPassReverse "/pim" "http://localhost:1512/pim" LoadModule headers_module modules/mod_headers.so# Apache sets X-Forwarded-Host and X-Forwarded-For headers by default, but not X-Forwarded-Proto which is required by Jetty RequestHeader set X-Forwarded-Proto "https" SSLEngine on ServerName localhost:443 SSLCertificateFile "${SRVROOT}/conf/ssl/server.crt" SSLCertificateKeyFile "${SRVROOT}/conf/ssl/server.key"</Virtualhost>Install SSL certificates on Product 360 Application Server directly
It is possible to setup SSL security on the Product 360 Application server, too. This is useful, if the connection between the Reverse Proxy and the Product 360 Server should be encrypted and secured, too.
To enable https, open the file <P360_SERVER>\configuration\HPM\NetworkConfig.xml.
<node identifier="pim-server1" host="localhost" > <web useHttps="true"> <http port="1512"/> <https port="8443" keyPassword="password" keystore="C:/Users/sroeck/.keystore" password="password"/> </web> <data-grid port="1801"/> <internal defaultRequestTimeout="300000"> <hlr-tcp port="1701" /> </internal> <default-role>CLIENTS_SERVER</default-role> <default-role>JOB_SERVER</default-role> </node>Please consult the Product 360 Configuration guide for a full list of all supported parameters.
Add the following lines to the Product 360 Server launch configuration (wrapper.conf) as JVM arguments to let Jetty know where the SSL certificate can be found:
-Djavax.net.ssl.keyStore=C:/Users/sroeck/.keystore-Djavax.net.ssl.keyStorePassword=passwordSetup Load Balancing
Please expose only the dedicated P360 interface you want to use externally.
If the P360 web application should be used expose only http://<hpmserver>:<hpmport>/pim to the public.
Never expose all endpoints running at http://<hpmserver>:<hpmport>.
Apache Web Server
If there is a cluster of Product 360 servers then the SSL/TLS-enabled Reverse Proxy described above can be configured as a load balancer with sticky sessions:
LoadModule proxy_module modules/mod_proxy.soLoadModule proxy_balancer_module modules/mod_proxy_balancer.soLoadModule proxy_http_module modules/mod_proxy_http.soLoadModule slotmem_shm_module modules/mod_slotmem_shm.soLoadModule lbmethod_byrequests_module modules/mod_lbmethod_byrequests.so #Apache 2.4Header add Set-Cookie "ROUTEID_HPMW=.%{BALANCER_WORKER_ROUTE}e; path=/" env=BALANCER_ROUTE_CHANGED<Proxy balancer://hpmwcluster> BalancerMember http://<hpmserver01>:<hpmwport01> route=1 BalancerMember http://<hpmserver02>:<hpmwport02> route=2 BalancerMember http://<hpmserver03>:<hpmwport03> route=3 BalancerMember http://<hpmserver04>:<hpmwport04> route=4 ProxySet stickysession=ROUTEID_HPMW</Proxy>ProxyPass /pim balancer://hpmwcluster/pimProxyPassReverse /pim balancer://hpmwcluster/pimHost and HTTP port for the nodes are defined in the corresponding elements of the NetworkConfig.xml. Please note that available scheduling algorithms and required modules differ between Apache httpd 2.4 and 2.2. Balancer manager provides some statistics and enables dynamic update of balancer members, please refer to the corresponding paragraph of the httpd documentation for details.
AWS ELB
Following the instructions on the official AWS ELB documentation pages at http://docs.aws.amazon.com/ElasticLoadBalancing/latest/DeveloperGuide/setting-up-elb.html
If you want to configure health check, make sure the ping is sent to the login page at http://server:1501/pim/login.
Make sure to configure Sticky Sessions and preferably use Application-Controlled Session Stickiness as described on http://docs.aws.amazon.com/ElasticLoadBalancing/latest/DeveloperGuide/elb-sticky-sessions.html.
The application cookie name is JSESSIONID, so the configuration might look like this:
"AppCookieStickinessPolicies": [ { "PolicyName": "my-app-cookie-policy", "CookieName": "JSESSIONID" } ]Troubleshooting Reverse Proxy / LB Setup and Product 360 Push issues
Product 360 uses Server-side push functionality implemented by the Vaadin framework. The supported modes can be configured in webfrontend.properties:
# Transport mode for server side push. Possible values: WEBSOCKET, STREAMING, LONG_POLLING. Default is STREAMING.web.vaadin.pushTransport=STREAMINGPlease note that WEBSOCKET is not supported.
In case you're experiencing issues after login, e.g. spinning loading indicator, time-outs, unresponsiveness or session time-outs, try one of the following things:
Switch pushTransport mode to STREAMING or LONG_POLLING. Requires a server restart to take changes in effect. LONG_POLLING seem to be more stable behind proxies than STREAMING.
Check if the issue can be reproduced in local network, when calling the app on the server directly.
Make sure, a proxy doesn't buffer requests.
In Apache, add "KeepAlive Off" in virtual host section.
In IIS, set "Response buffer treshold" to 0
Turn http compression off, if enabled.

Some general hints regarding Push issues with Vaadin can be found on https://vaadin.com/wiki/-/wiki/Main/Working+around+push+issues